Merge the obfuscate process into the publishing flow
Understanding the fundamentals of MSBuild 1 is good for comprehending the merging of the obfuscate process into the publishing flow. I don’t want to talk about MSBuild in the post (But I added some comments for you to catch the action briefly), so just copy the following code into the <Project> element in the .csproj file is good to go.
<Target Name="BitMono" AfterTargets="AfterBuild" Condition="'$(Configuration)'=='Release' AND $(TargetFramework.Contains('windows')) == true">
<ItemGroup>
<Sourcelibs Include="$(TargetDir)**\*.*" />
</ItemGroup>
<!-- Make folder for BitMono reference -->
<ItemGroup>
<BitMonoReference Include="$(TargetDir)libs" />
</ItemGroup>
<MakeDir Directories="@(BitMonoReference)" />
<!-- Copy all library files from Sourcelibs folder to BitMonoReference folder -->
<Copy SourceFiles="@(Sourcelibs)" DestinationFolder="@(BitMonoReference)" />
<!-- Execute obfuscation -->
<Exec WorkingDirectory="$(TargetDir)" Command="BitMono.CLI -f $(ProjectName).dll" />
<!-- Once BitMono finish the work, remove the BitMonoReference folder -->
<RemoveDir Directories="@(BitMonoReference)" />
<ItemGroup>
<BitMonoOutput Include="$(TargetDir)output\*.*" />
</ItemGroup>
<!-- Copy the output files generate by BitMono to TargetDir -->
<Copy SourceFiles="@(BitMonoOutput)" DestinationFolder="$(TargetDir)" />
</Target>
Publish the Windows app
Publish .NET MAUI Windows App with MSIX format
Set the Configuration as
ReleaseandAny CPU Publish MSIX Step 1
Publish MSIX Step 1Open the Solution Explorer and right-click the project and click
Publishin the selection list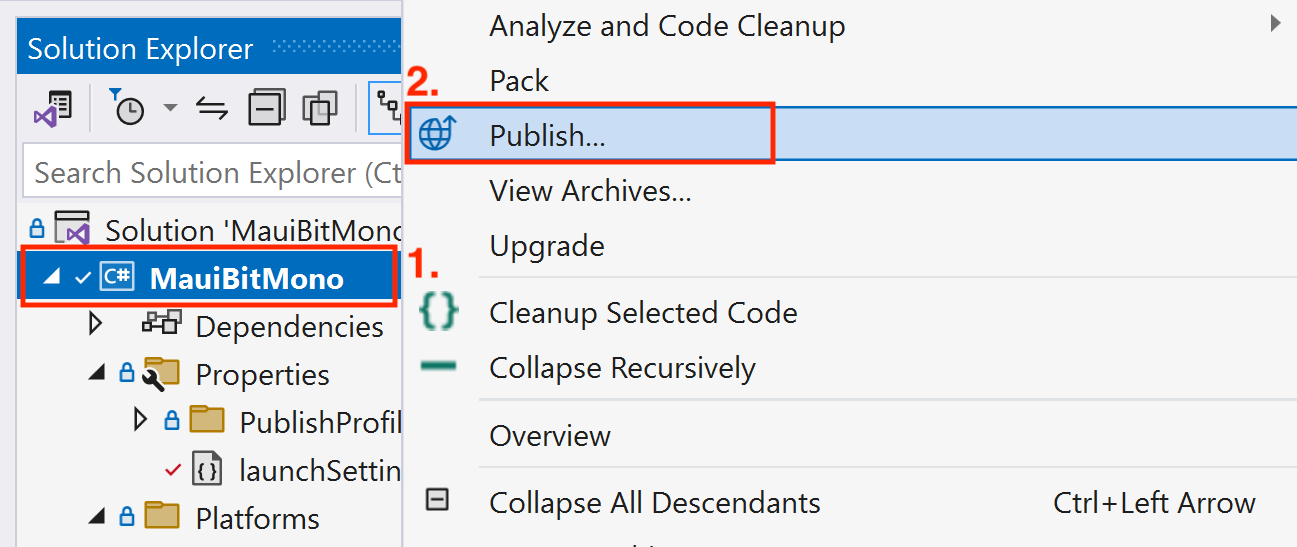 Publish MSIX Step 2
Publish MSIX Step 2Select
Microsoft Store under a new app nameselection and clickNext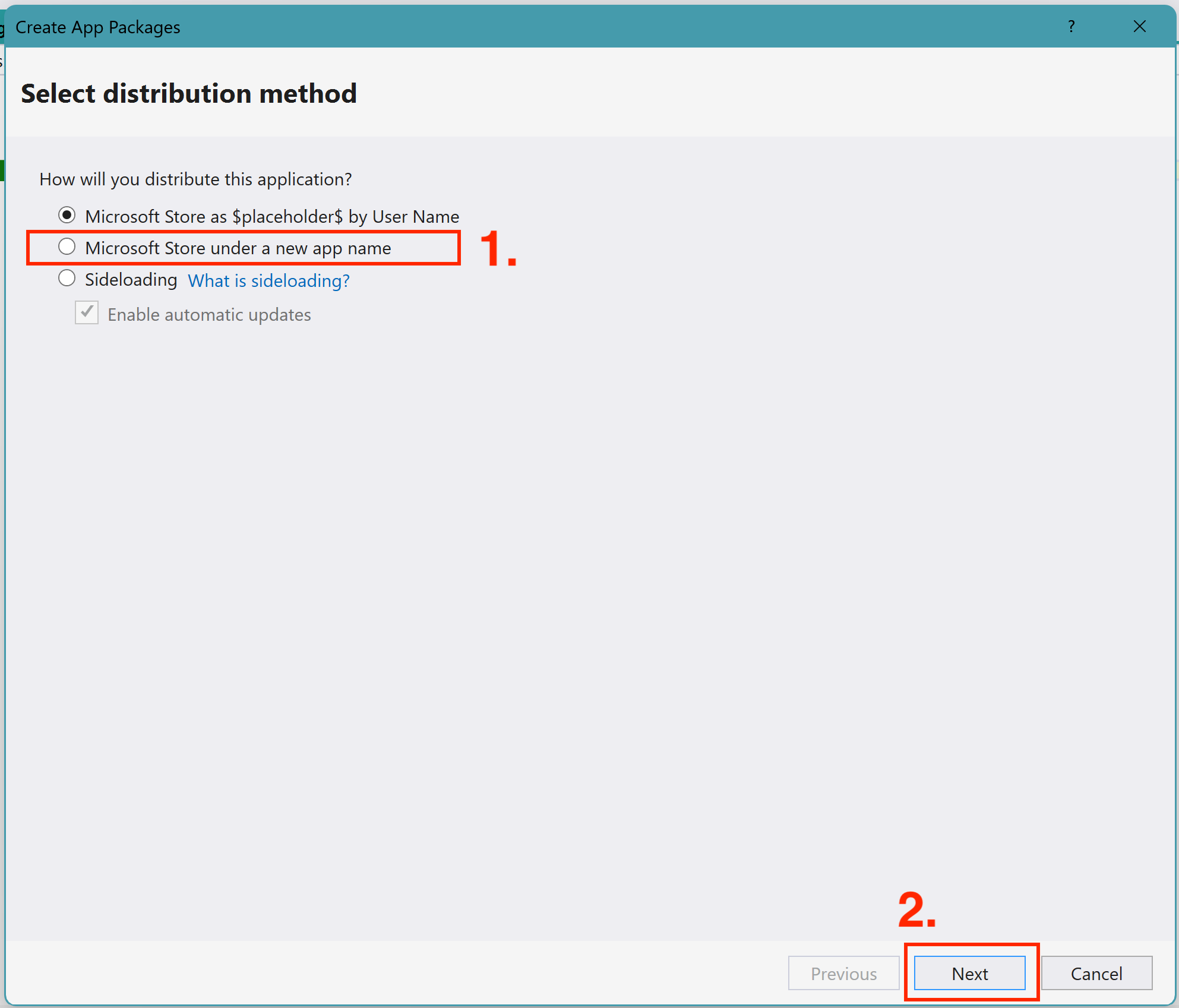 Publish MSIX Step 3
Publish MSIX Step 3Select the app name (You should create and register the app name on the Microsoft Partner Center first) and click
Next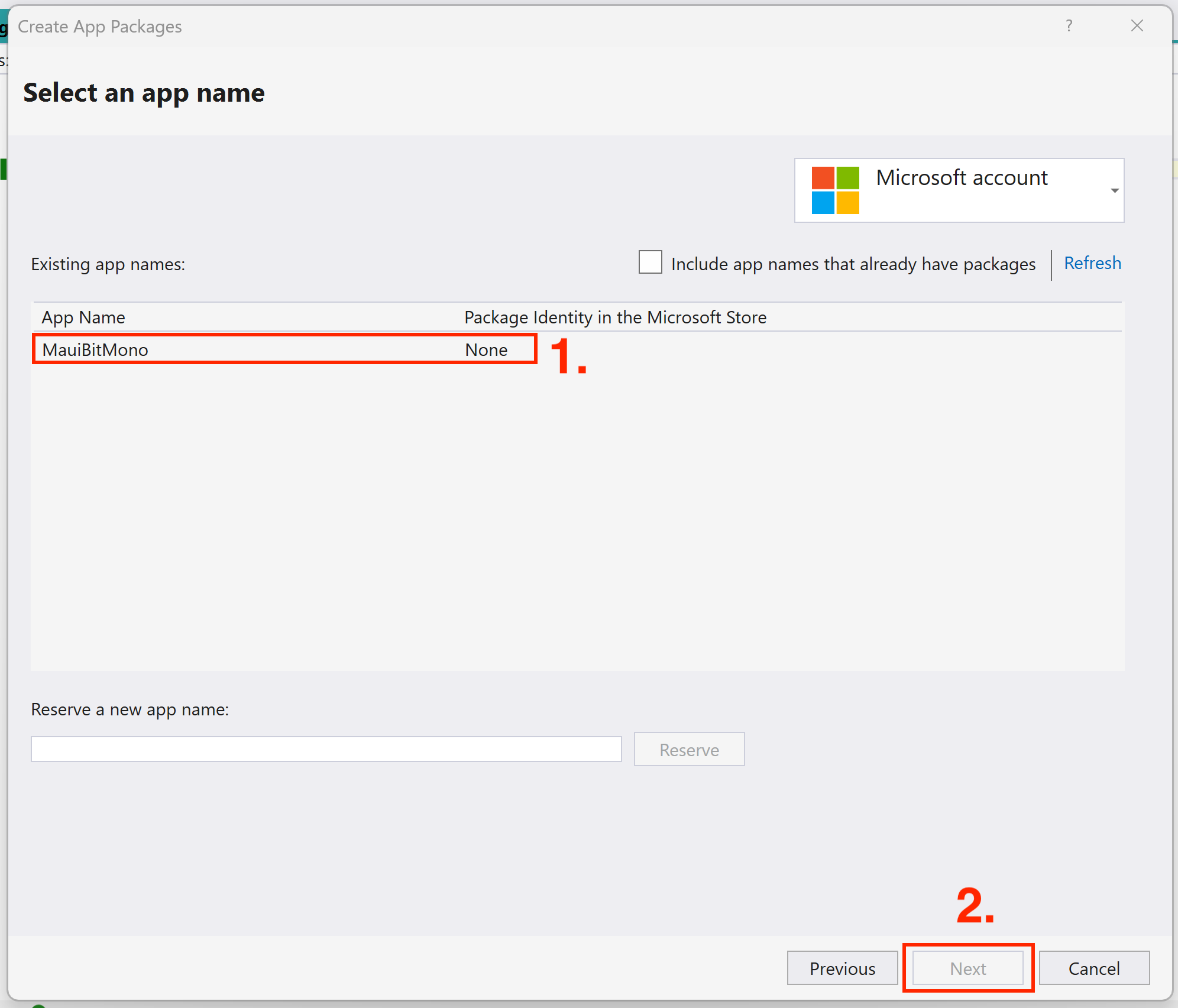 Publish MSIX Step 4
Publish MSIX Step 4Set up the version number and create the publishing profile. Please be sure the publishing profile is related to the “Release” setting (You can refer to the following image for more details).
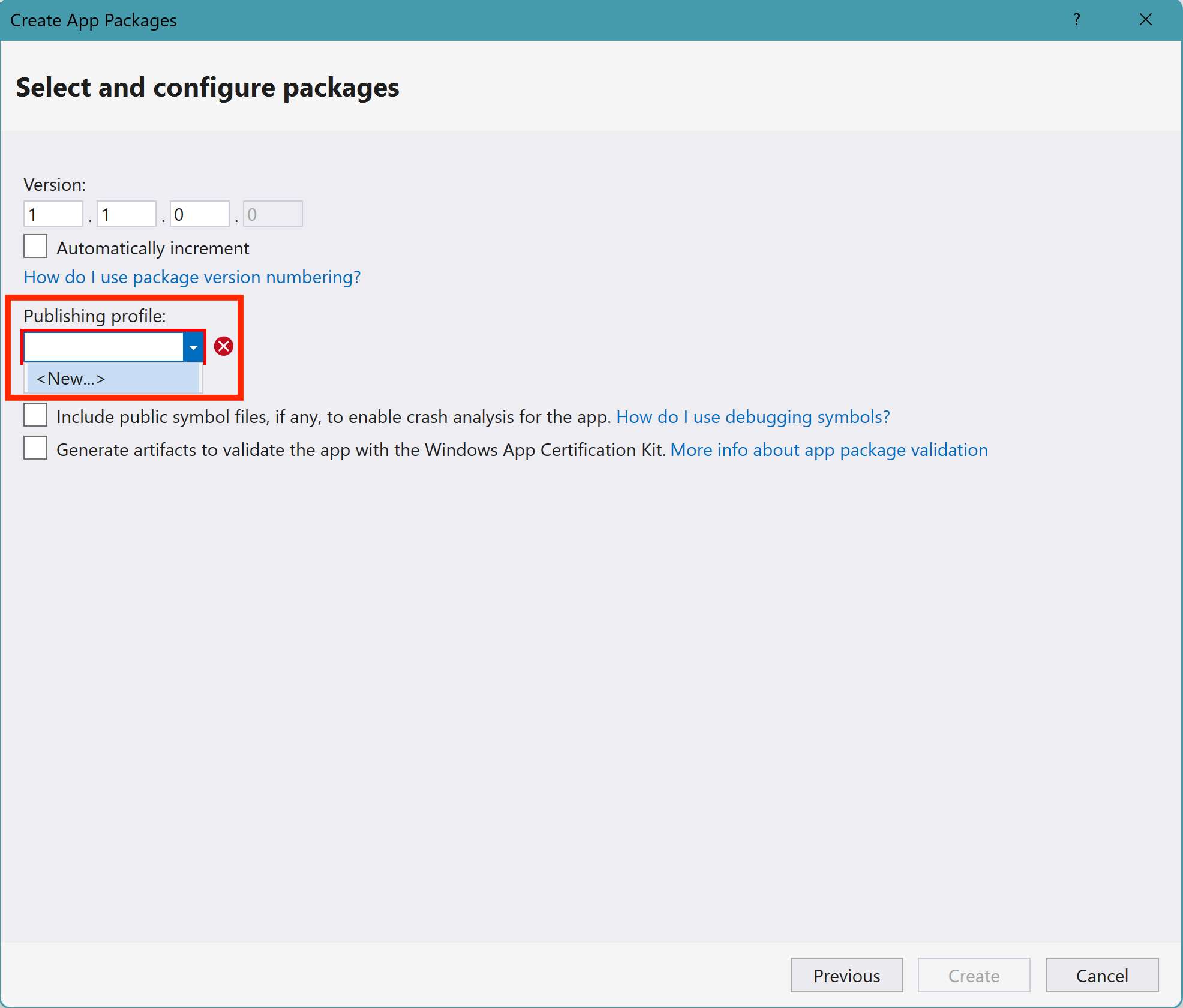
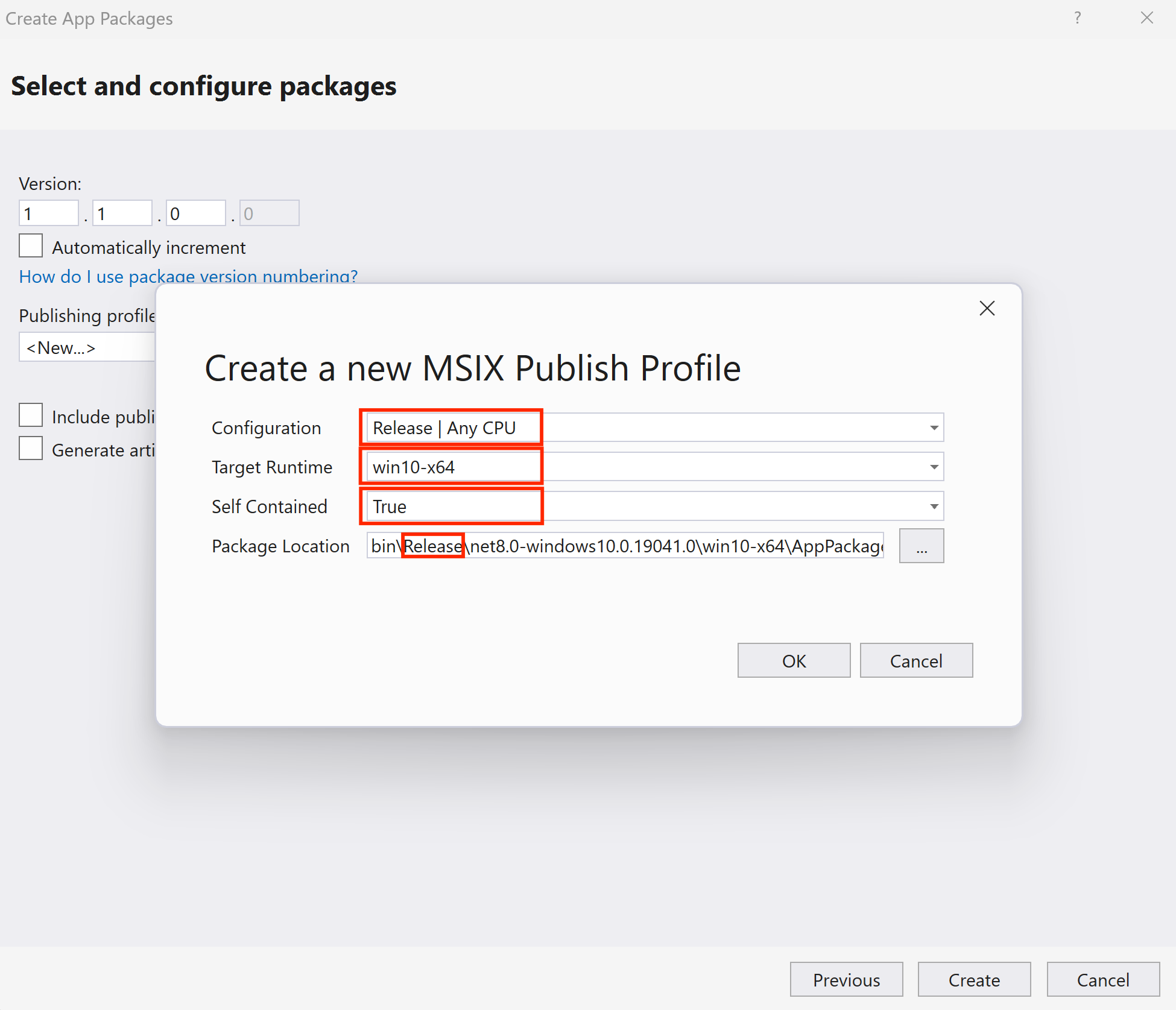 Publish MSIX Step 5 & 6
Publish MSIX Step 5 & 6Once finish the setup, click
OKandCreate
Publish .NET MAUI Windows App Unpackaged
Publishing the .NET MAUI Windows App unpackaged instead of MSIX.
- Modify the
launchSettings.json(InPropertiesfolder in MAUI project) as the following:
{
"profiles": {
"Windows Machine": {
// Don't use MSIX, Comment the following line
// "commandName": "MsixPackage",
"commandName": "Project",
"nativeDebugging": false
}
}
}
Add the following code into the
<PropertyGroup>element in.csprojfile:<WindowsPackageType>None</WindowsPackageType>Set the Configuration as
ReleaseandAny CPUand then click the▶️ Windows Machinebutton Publish .NET MAUI Windows App Unpackaged
Publish .NET MAUI Windows App Unpackaged
Discussion
Obfuscation
In this demo, we disable all the protection but enable StringsEncryption to demonstrate and discuss the Bitmono Obfuscation.
During the publishing process, Bitmono will run and obfuscate the .NET assembly (dll) after your MAUI project is built successfully. (You can see the obfuscation log in the Build console window in the Visual Studio)
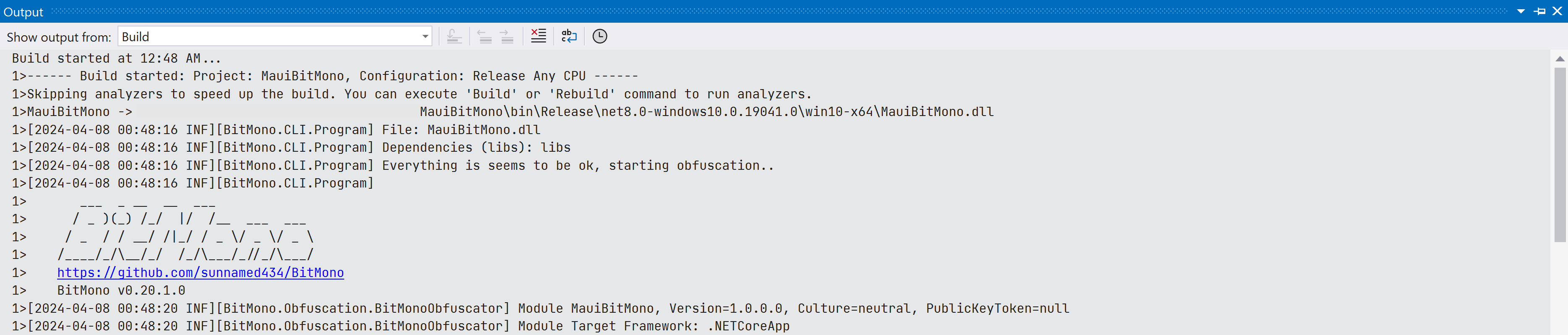 BitMono Log (Started)
BitMono Log (Started)
Once Bitmono obfuscates successfully, you will see the log like the following:
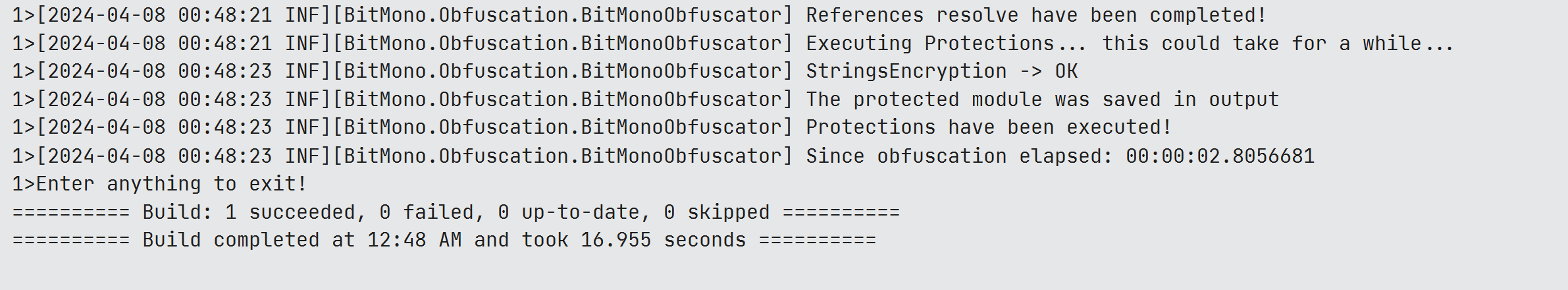 BitMono Log (Finished)
BitMono Log (Finished)
Testing the app
Please locate the publishing folder and open the app to confirm that it can launch and its behavior is correct and expected.
Packaged app (MSIX)
Please refer to the Microsoft technical documentation to install the packaged app and then open it for testing.
Unpackaged app
Open the exe file in the publishing folder. (MauiBitMono\bin\Release\net8.0-windows10.0.19041.0\win10-x64\MauiBitMono.exe in this demo)
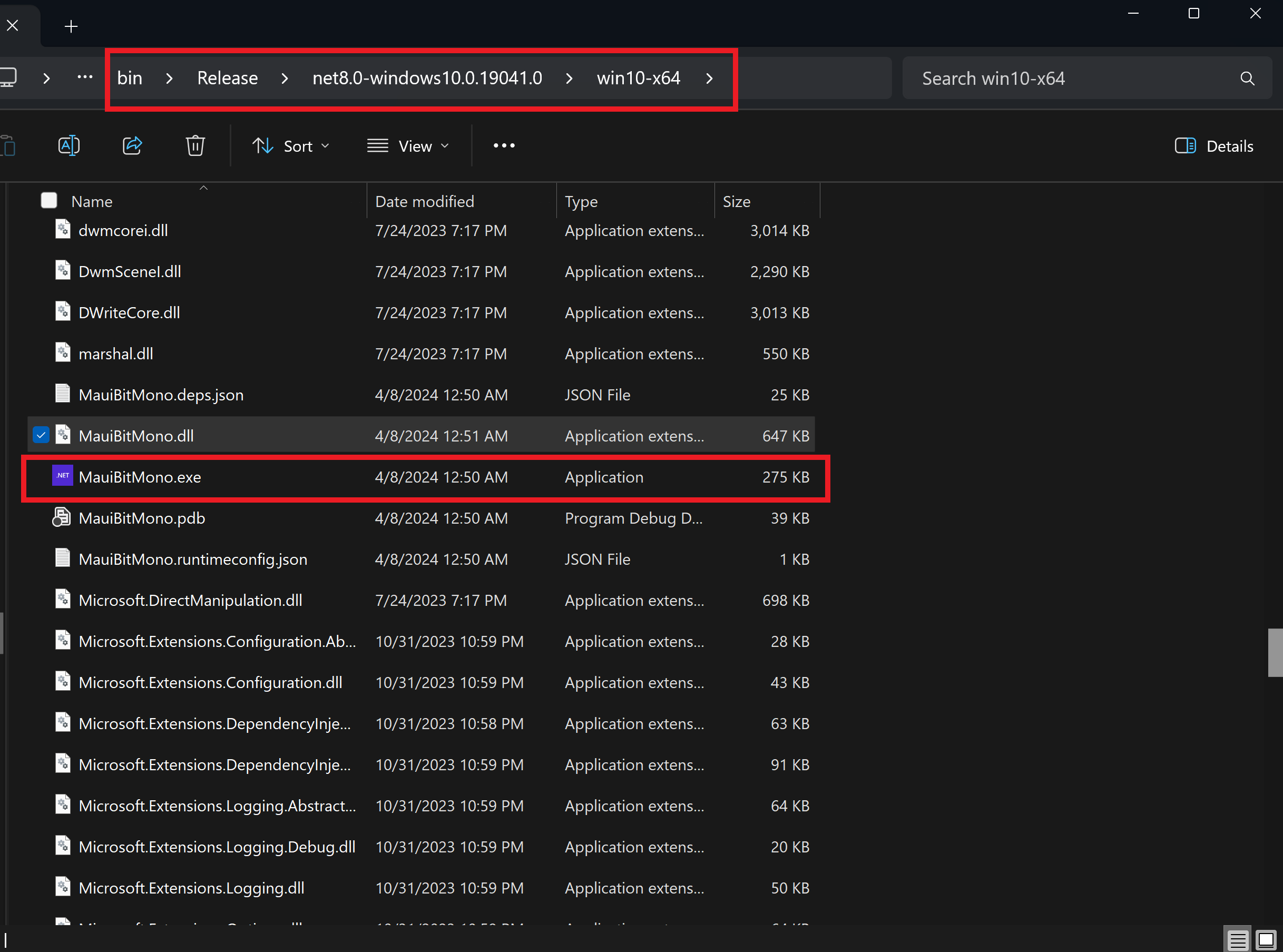 Open the App
Open the App
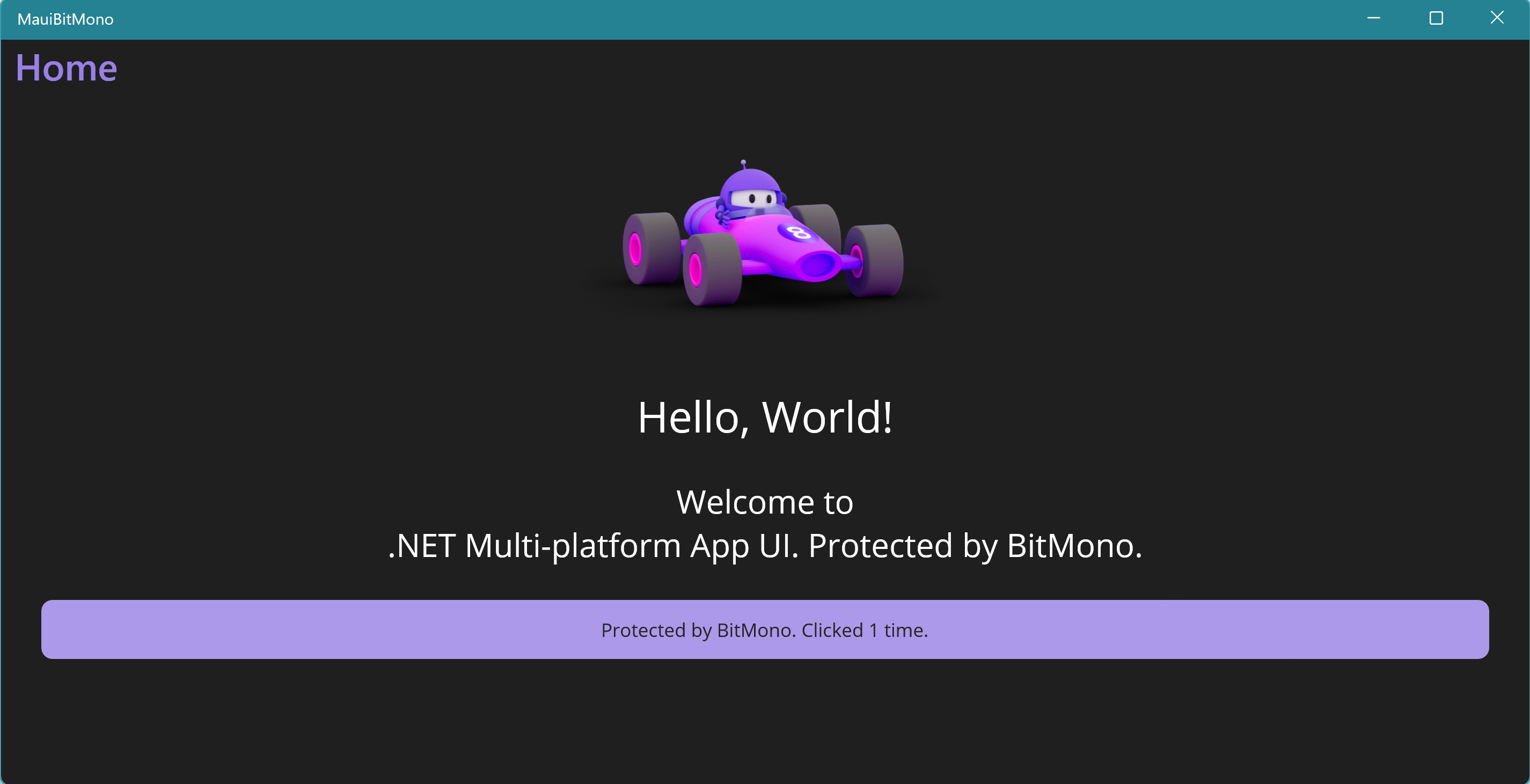 Confirm Everything is OK of the App
Confirm Everything is OK of the App
Troubleshooting
There are many reasons why the app does not launch correctly; one possible is caused by obfuscation. Please use Windows Reliability Monitor to identify the cause of software failures. 2 If the failure is caused by obfuscation, please create an issue from the BitMono repository so that the community or maintainer can fix it.
Verification and Comparison
We can drag and drop the .NET assembly (dll) into the .NET decompiler (such as ILSpy) to verify the code obfuscation (MauiBitMono\bin\Release\net8.0-windows10.0.19041.0\win10-x64\MauiBitMono.dll in this demo).
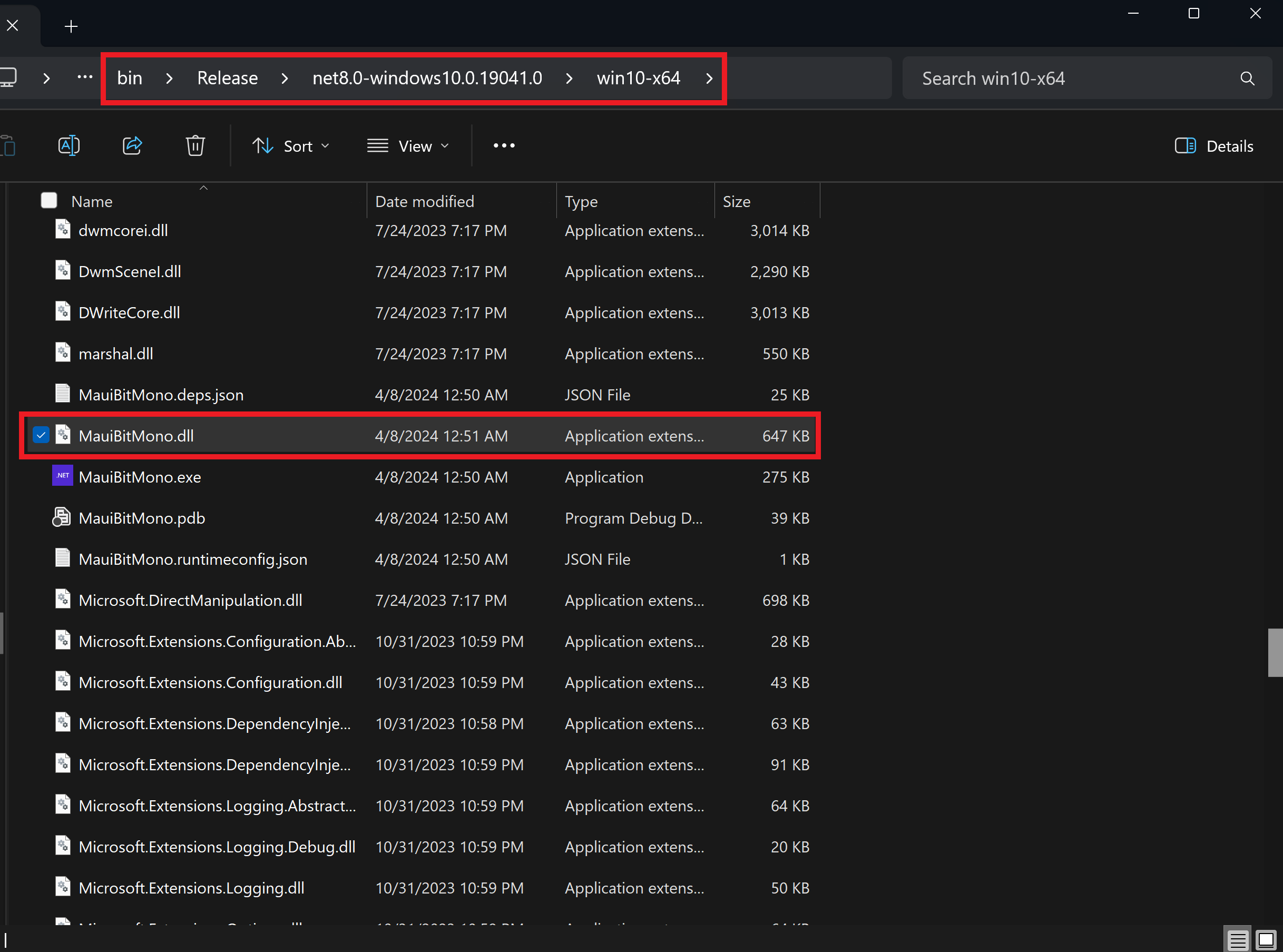 Decompile the DLL
Decompile the DLL
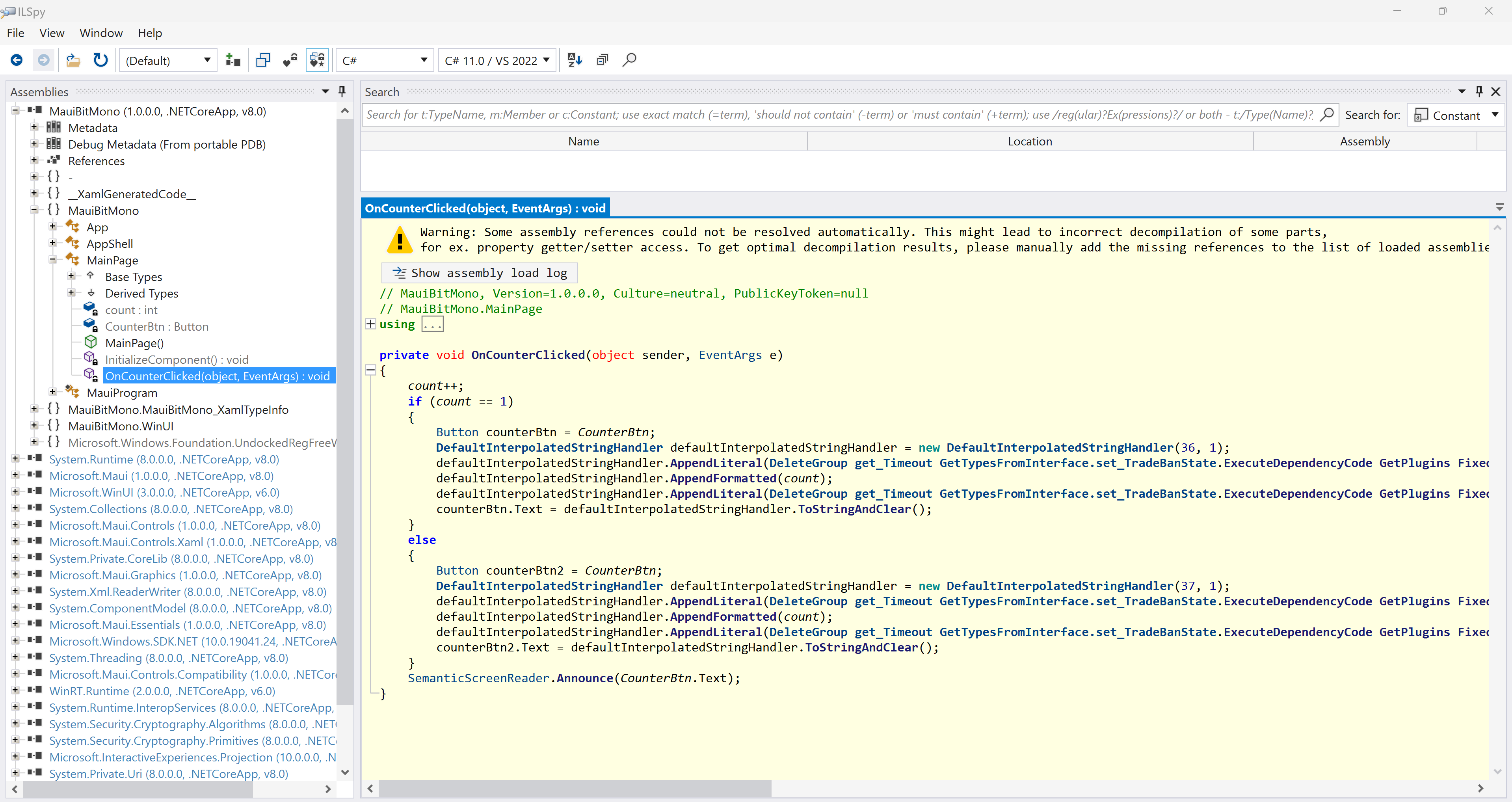 Decompile by ILSpy
Decompile by ILSpy
In this demo, we create a simple MAUI project. The original code of function private void OnCounterClicked(object sender, EventArgs e) in file MainPage.xaml.cs is shown as the following:
private void OnCounterClicked(object sender, EventArgs e)
{
count++;
if (count == 1)
CounterBtn.Text = $"Protected by BitMono. Clicked {count} time.";
else
CounterBtn.Text = $"Protected by BitMono. Clicked {count} times.";
SemanticScreenReader.Announce(CounterBtn.Text);
}
After obfuscation, the corresponding function code comes from the ILSpy decompiler result is shown as the following. We can see that the string in the code is obfuscated and cannot identify the original text:
private void OnCounterClicked(object sender, EventArgs e)
{
count++;
if (count == 1)
{
Button counterBtn = CounterBtn;
DefaultInterpolatedStringHandler defaultInterpolatedStringHandler = new DefaultInterpolatedStringHandler(36, 1);
defaultInterpolatedStringHandler.AppendLiteral(DeleteGroup get_Timeout GetTypesFromInterface.set_TradeBanState.ExecuteDependencyCode GetPlugins FixedUpdate.SetCooldown(global::<Module>.<>c.RemovePlayerFromGroup get_MemberSince checkCommandMappings.GetGroup, global::<Module>.<>c.get_Instance GetOpenWindows IsDependencyLoaded.Start, global::<Module>.<>c.set_AvatarFull get_HoursPlayedLastTwoWeeks ExternalLog.set_MemberSince));
defaultInterpolatedStringHandler.AppendFormatted(count);
defaultInterpolatedStringHandler.AppendLiteral(DeleteGroup get_Timeout GetTypesFromInterface.set_TradeBanState.ExecuteDependencyCode GetPlugins FixedUpdate.SetCooldown(global::<Module>.<>c.LoadDefaults get_Help GetTypesFromInterface.Load, global::<Module>.<>c.get_Instance GetOpenWindows IsDependencyLoaded.Start, global::<Module>.<>c.set_AvatarFull get_HoursPlayedLastTwoWeeks ExternalLog.set_MemberSince));
counterBtn.Text = defaultInterpolatedStringHandler.ToStringAndClear();
}
else
{
Button counterBtn2 = CounterBtn;
DefaultInterpolatedStringHandler defaultInterpolatedStringHandler = new DefaultInterpolatedStringHandler(37, 1);
defaultInterpolatedStringHandler.AppendLiteral(DeleteGroup get_Timeout GetTypesFromInterface.set_TradeBanState.ExecuteDependencyCode GetPlugins FixedUpdate.SetCooldown(global::<Module>.<>c.set_Timeout FixedUpdate LoadPlugin.FireEventCallback, global::<Module>.<>c.get_Instance GetOpenWindows IsDependencyLoaded.Start, global::<Module>.<>c.set_AvatarFull get_HoursPlayedLastTwoWeeks ExternalLog.set_MemberSince));
defaultInterpolatedStringHandler.AppendFormatted(count);
defaultInterpolatedStringHandler.AppendLiteral(DeleteGroup get_Timeout GetTypesFromInterface.set_TradeBanState.ExecuteDependencyCode GetPlugins FixedUpdate.SetCooldown(global::<Module>.<>c.LogWarning Save get_ConnectedTime.get_AvatarMedium, global::<Module>.<>c.get_Instance GetOpenWindows IsDependencyLoaded.Start, global::<Module>.<>c.set_AvatarFull get_HoursPlayedLastTwoWeeks ExternalLog.set_MemberSince));
counterBtn2.Text = defaultInterpolatedStringHandler.ToStringAndClear();
}
SemanticScreenReader.Announce(CounterBtn.Text);
}
What BitMono does?
In general, BitMono encrypts strings in code using basic AES encryption. It converts the string to a byte array and then uses the cryptographic services provided by System.Security.Cryptography to encrypt the byte array. You can see the implementation here and here.
Conclusion
In this tutorial, we use BitMono to obfuscate the Windows app made with the .NET MAUI framework. We also merge the obfuscate process into the publishing flow by adding the MSBuild XML code to the .csproj project file. In our demo, we enable the StringsEncryption protection to demonstrate the obfuscation and then try to decompile the obfuscated (protected) .NET assembly. The ILSpy decompile result shows that the string in the code is obfuscated and we cannot identify the original text.
You can enable more protection on your application to decrease the harm from reverse engineering, but again, please be careful of the protection’s compatibility and the impact when protection is enabled (such as slowing down the app’s performance).
Bear in mind that nothing is uncrackable; only the software on the server side is well-protected and unbreakable generally. Code obfuscation techniques cannot completely eliminate the risk and harm of reverse engineering. Even if the green-hand reverse engineer, just opens the IDA-Pro 3 for example, who can browse your code like a hot knife through butter. Obfuscation ONLY lets them slow down the speed of analyzing and feel pain when trying to analyze the code.
Download the Demo Example
The demo throughout this tutorial is available on GitHub. 4
Reference
Microsoft. (2024). Common MSBuild project properties. Retrieved from https://web.archive.org/web/20240318130631/https://learn.microsoft.com/en-us/visualstudio/msbuild/common-msbuild-project-properties?view=vs-2022 ↩︎
Craig Marcho. (2019). Using Reliability Monitor for Troubleshooting. Retrieved from https://web.archive.org/web/20230524035106/https://techcommunity.microsoft.com/t5/ask-the-performance-team/using-reliability-monitor-for-troubleshooting/ba-p/372962 ↩︎
Wikipedia contributor. (2024). The Interactive Disassembler (IDA). Retrieved from https://web.archive.org/web/20240330203125/https://en.wikipedia.org/wiki/Interactive_Disassembler ↩︎
Shing Ming (Tim), Wong. (2024). MauiBitMono - The tutorial on using BitMono obfuscator to protect .NET MAUI Apps. Retrieved from https://github.com/shingming/MauiBitMono ↩︎